Floating rules can run on multiple interfaces for inbound outbound or both directions. Floating Rules are a special type of firewall rules and typically perform additional actions not available with simple rules directly on the other interfaces or group tabs. Home network firewall rules.
Home Network Firewall Rules, Your list is good although you might want to add DNS and also NTP if you are want to sync time. You should allow the outbound traffic for the protocols that you will be using. Source IP address or range of IP addresses. A good firewall policy also has a formal.
 Mcafee Kb Unable To Print Or Access Network Devices After You Install Mcafee Security Software For Mac Ts102251 From service.mcafee.com
Mcafee Kb Unable To Print Or Access Network Devices After You Install Mcafee Security Software For Mac Ts102251 From service.mcafee.com
In general most firewall configurations prefer simple rules over the floating ones. This strategy is the principle of least privilege and it forces control over network traffic. Devices implementing mDNS need to listen to these packets and respond where appropriate. Equation 1 A Portion of the HOME_OUT Firewall Ruleset.
Devices implementing mDNS need to listen to these packets and respond where appropriate.
Read another article:
The home network or small area network enables multiple devices eg. Source IP address or range of IP addresses. This strategy is the principle of least privilege and it forces control over network traffic. The rules in this ruleset are applied not shown here to the output side of both of the eth3 and eth4 interfaces ie switch0. You should allow the outbound traffic for the protocols that you will be using.
 Source: docs.microsoft.com
Source: docs.microsoft.com
A layer 4 firewall uses the following parameters for an access rule. Inbound allow rules. Floating rules can run on multiple interfaces for inbound outbound or both directions. The home network or small area network enables multiple devices eg. Best Practices For Configuring Windows Defender Firewall Windows Security Microsoft Docs.
 Source: youtube.com
Source: youtube.com
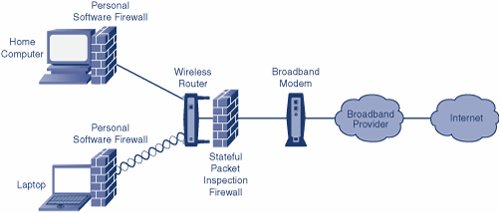
Essentially a firewall is your shield to the outside network. Inbound allow rules. In this tutorial you will learn how you to build and setup a home or small area network and connect it to the Internet. Its most commonly implemented as Bonjour Apple and Avahi Linux. Setup Iot Vlans And Firewall Rules With Unifi Ultimate Smart Home Network Part Three Youtube.
 Source: flylib.com
Source: flylib.com
In general most firewall configurations prefer simple rules over the floating ones. PCstablets etc to connect to each other and also to connect to the internet. Therefore a firewall with 3 network interfaces allows you to create 2 physical subnets. All traffic that comes into your network is scanned by the. Putting Firewalls To Work Home Network Security Simplified.
 Source: informaticar.net
Source: informaticar.net
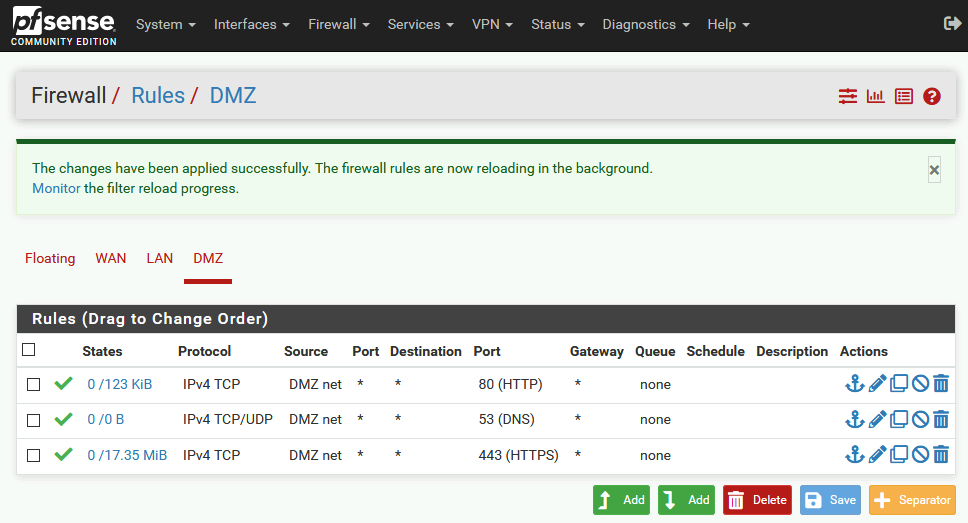
A layer 4 firewall uses the following parameters for an access rule. PfSense ie making sense of packet filtering is a customized version of FreeBSD tailored specifically for use as a perimeter firewall and router and managed almost entirely. All traffic that comes into your network is scanned by the. Allow Program through Firewall. How To Setup Dmz On Pfsense It Blog.
 Source: netosec.com
Source: netosec.com
Your list is good although you might want to add DNS and also NTP if you are want to sync time. The rules that you use to define network access should be as specific as possible. Therefore a firewall with 3 network interfaces allows you to create 2 physical subnets. 20180226 This post has been amended to reflect changes in pfSense version 242 iceflatline This post will describe how to install and perform initial configuration of pfSense for use in a home network. Setup Vlan Subnets For Home Network Netosec.
 Source: home-network-help.com
Source: home-network-help.com
PCstablets etc to connect to each other and also to connect to the internet. PfSense ie making sense of packet filtering is a customized version of FreeBSD tailored specifically for use as a perimeter firewall and router and managed almost entirely. When first installed networked applications and services issue a listen call specifying the protocolport information required for them to function properly. A layer 4 firewall uses the following parameters for an access rule. How To Enable Windows Firewall In Windows 7.
 Source: service.mcafee.com
Source: service.mcafee.com
Specify as many parameters as possible in the rules. Floating Rules are a special type of firewall rules and typically perform additional actions not available with simple rules directly on the other interfaces or group tabs. Source IP address or range of IP addresses. All traffic that comes into your network is scanned by the. Mcafee Kb Unable To Print Or Access Network Devices After You Install Mcafee Security Software For Mac Ts102251.
 Source: softwaretestinghelp.com
Source: softwaretestinghelp.com
When first installed networked applications and services issue a listen call specifying the protocolport information required for them to function properly. Equation 1 A Portion of the HOME_OUT Firewall Ruleset. In this tutorial you will learn how you to build and setup a home or small area network and connect it to the Internet. Firewall requires a minimum of 2 network interfaces 1 for connecting to WAN 1 for connecting to LAN internal home network. A Complete Guide To Firewall How To Build A Secure Networking System.
 Source: sciencedirect.com
Source: sciencedirect.com
Firewall rules should be documented tracking the rules purpose what services or applications it affects affected users and devices date when the rule was added the rules expiration date if applicable and who added the rule. A layer 4 firewall uses the following parameters for an access rule. Its most commonly implemented as Bonjour Apple and Avahi Linux. Firewall requires a minimum of 2 network interfaces 1 for connecting to WAN 1 for connecting to LAN internal home network. Network Firewall An Overview Sciencedirect Topics.
 Source: protectli.com
Source: protectli.com
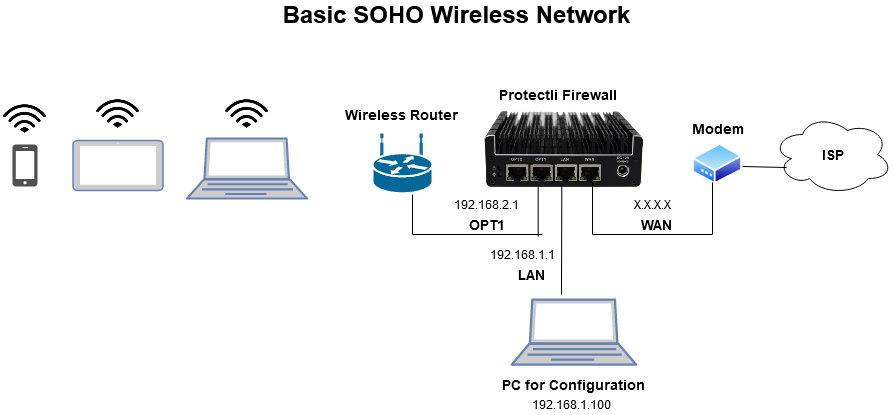
A network firewall is working the same way. Firewall rules should be documented tracking the rules purpose what services or applications it affects affected users and devices date when the rule was added the rules expiration date if applicable and who added the rule. Specify as many parameters as possible in the rules. A layer 4 firewall uses the following parameters for an access rule. Basic Soho Wireless Network Protectli.
 Source: softwaretestinghelp.com
Source: softwaretestinghelp.com
You should allow the outbound traffic for the protocols that you will be using. You should allow NO inbound traffic. To use domain name filtering for traffic from outside the VPC where youve deployed Network Firewall you must manually set the HOME_NET variable for the rule group. Floating rules can run on multiple interfaces for inbound outbound or both directions. A Complete Guide To Firewall How To Build A Secure Networking System.
 Source: support.hp.com
Source: support.hp.com
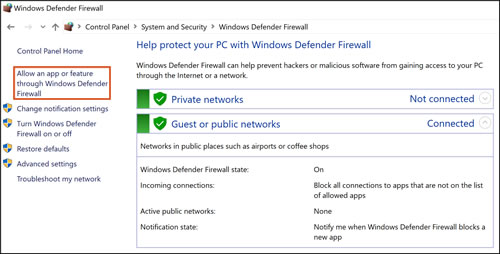
The main reason most people will ever mess with the firewall is to allow a program to work through the firewall. The rules in this ruleset are applied not shown here to the output side of both of the eth3 and eth4 interfaces ie switch0. This means that we need to setup a firewall rule for UDP port 5353 to allow HomeKit clients to find the HomeKit accessory in this case Home Assistant. The rules that you use to define network access should be as specific as possible. Hp Printers Firewall Blocking Driver Install Or Printer Function Windows Hp Customer Support.
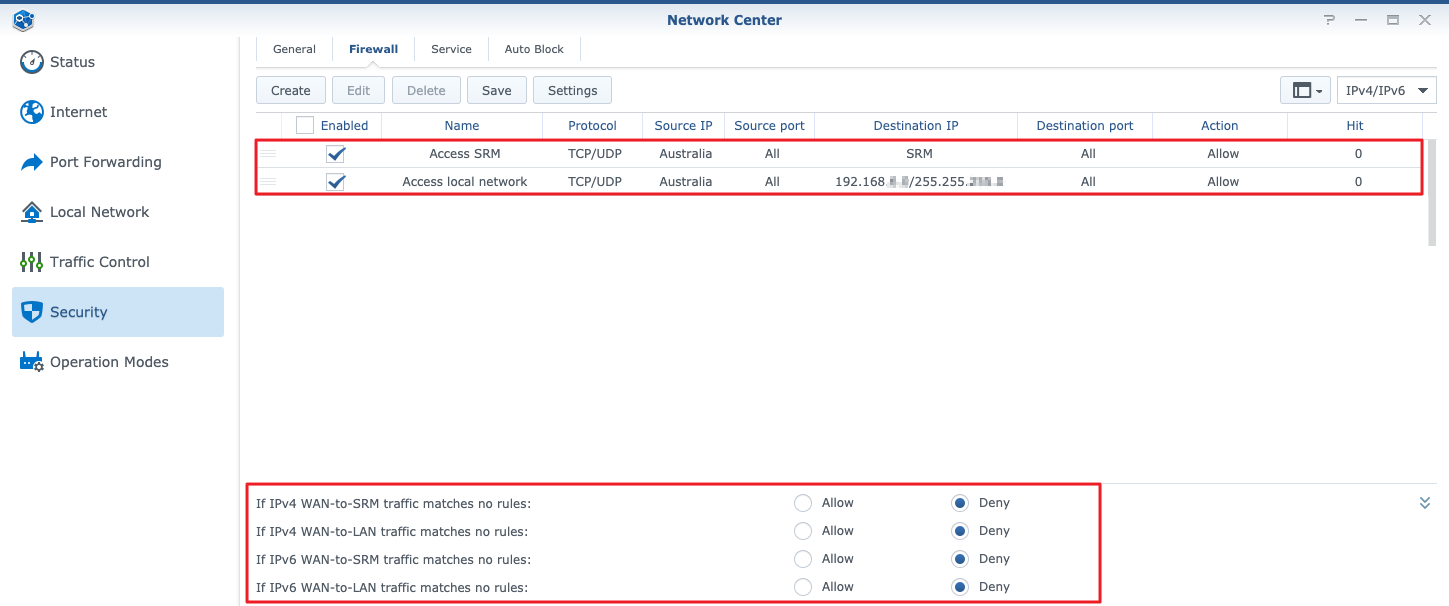 Source: kb.synology.com
Source: kb.synology.com
You should allow NO inbound traffic. The rules in this ruleset are applied not shown here to the output side of both of the eth3 and eth4 interfaces ie switch0. Allow Program through Firewall. Each extra network interface would allow firewall to create an additional physical sub-network. How Do I Create Firewall Rules To Allow Or Deny Ip Addresses To Access Srm Or The Local Network Synology Knowledge Center.
 Source: networkworld.com
Source: networkworld.com
Each extra network interface would allow firewall to create an additional physical sub-network. Today almost every home and small office has a local network and an Internet connection. When first installed networked applications and services issue a listen call specifying the protocolport information required for them to function properly. The rules that you use to define network access should be as specific as possible. 4 Tools For Managing Firewall Rules Network World.
 Source: softwaretestinghelp.com
Source: softwaretestinghelp.com
It keeps the area behind it the LAN safe from bad stuff that would like to get into a network. Source IP address or range of IP addresses. PfSense ie making sense of packet filtering is a customized version of FreeBSD tailored specifically for use as a perimeter firewall and router and managed almost entirely. The most common use case for this is a central firewall VPC with traffic coming from other VPCs through a transit gateway. A Complete Guide To Firewall How To Build A Secure Networking System.







